[March 2019] Unfortunately Dell have now withdrawn support for old Wyse products and shut down the old Wyse support server: see here. As a consequence I've removed the old now dead links in the text below but left the article in case you may be able to track down the firmware elsewhere.
This section covers various salient elements of the Wyse 3125SE Firmware and the way in which it behaves. As Wyse supply similar underlying hardware and firmware to Compaq the words here are very similar to those in the Evo T20 section.
The 3125SE doesn't have a standard PC BIOS. On power up it will only boot the embedded operating system from it's flash memory so there is no "just plug in a USB memory stick with a bootable version of Linux and you're away" here. (Note: Some of the higher end models do offer network booting via PXE support, but my Windows CE based unit doesn't).
However Wyse do provide a basic "get-out-of-jail free" mechanism as a way of both upgrading system files and recovering from all but the most severe of flash memory corruption. Generally it is this mechanism - referred to as NETXFER - that we use to get our Linux code onto the 3125SE. We use it to replace the operating system file that the 3125SE "boots" by one of our own which contains the code we need to get Linux running.
Note: Wyse systems actually appear to run with two BIOSes. There is the simple "power up" version which includes the embedded Netxfer code. This is what is in place if you download and run code using Netxfer. However, when booting from flash, the simple BIOS is replaced by a more comprehensive one that is loaded from the flash memory prior to booting the operating system. The net effect of this is that you will find (sometimes significant) differences between the two environments that you will have to cope with in your start-up code. (See also the Evo T20 section for some more words on this).
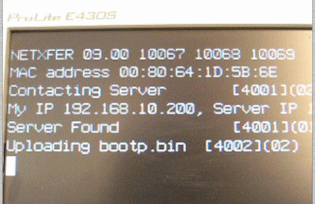 This is really a very simple loading mechanism which is invoked by pressing the P key
on the keyboard whilst the 3152SE is restarting. When the 3152SE recognises this the following happens:
This is really a very simple loading mechanism which is invoked by pressing the P key
on the keyboard whilst the 3152SE is restarting. When the 3152SE recognises this the following happens:
NETXFER.EXE is the name of the utility that Wyse supply to provide a packaged DHCP/TFTP server that runs in a Windows environment. I haven't bothered with it. As described here it is very easy to setup the required servers in a Linux environment.
A hint of what's in the file can be found in the Re-imaging Utility (3125SE) download (NetXfer.zip) which is at the bottom of the list of files on the Wyse 3152SE support page.
Included in the pack is the utility img2UTC.exe and the batch file mkutc.bat. From this it would seem that this "bundle" file format is referred to as UTC.
There are set of tools available from here that allow you to extract files from a bundle and build new bundles incorporating your own replacement files. However these days I use my own set of tools that can (not surprisingly!) be found in the tools section of this website.
If you check Wyse's site ( here) you'll find you have the option of downloading code for 3125SE (CE) or 3125SE. I arbitrarily picked the latter and downloaded the file 541Wye34_3125_FTP.exe. This ultimately unpacks to the binary image F576_Wye74.bin. The bundle in this image comprises 700 files - of which we're only interested in the first few few....
This seems to be a NetXfer image, skipping the NetXfer bootstrap. Offset Size Checksum SysFlg BiosFlag Time Filename 000074d8 00040000 ceb26146 010000 00010000 467ba3c1 frl_code.ce 000474d8 00000014 fdfc0bf5 010000 00020000 467ba3c1 k 000474ec 008177a7 ffeb6b5d 010000 00020000 467ba3c1 nk.bin 0085ec94 000097a0 248ba8c2 010000 00020000 467ba3c1 poweron.bmp 00868434 00040000 179a7ed8 010000 00020000 467ba3c1 frl_code.bin ...... ......
With other models with larger flash chips (and hence more files) the bundle holds a complete image of each flash chip. In this case they are named FILESYS0.IMG, FILESYS1.IMG and FILESYS2.IMG. In these circumstances we use the Linux loop device to mount the and access the contents of the file system image.